Test Your Defenses
Our Modern Approach to PenTesting
Our automated pentration testing methodology looks for sensitive data, performs exploits, conducts man-in-the-middle attacks, crack password hashes, escalates privileges on the network, and even impersonates users to find sensitive data. It goes beyond identifying vulnerabilities by actually exploiting them to demonstrate what happens if an attacker got access to the network.
Our platform is backed by consultants with over 10 years of experience, holding certifications ranging from CISSP, eCPPT, OSCP, OSCE, CEH, and more.
A more efficient pen-testing methodology
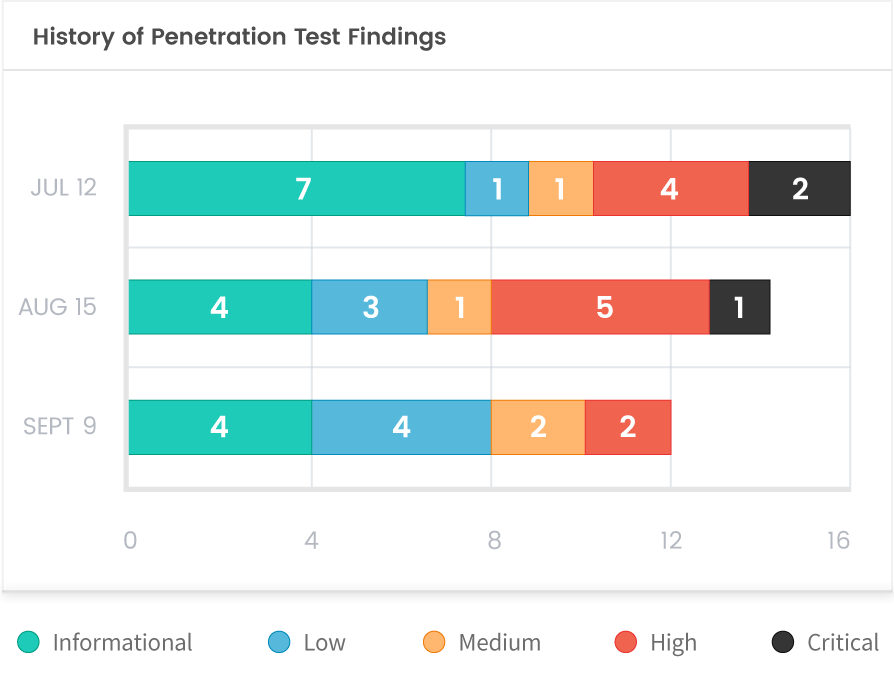
Conduct monthly security assessments to understand your risks to cyber attacks in near real-time
Traditional assessments only allow organizations to demonstrate a point-in-time snapshot of the environment. vPenTest enables monthly or on-demand risk management by allowing organizations to perform a full-scale network penetration tests with a few clicks. The platform measures the effectiveness of compensating controls through its exploitation techniques while minimizing risk through the implementation of compensating controls.
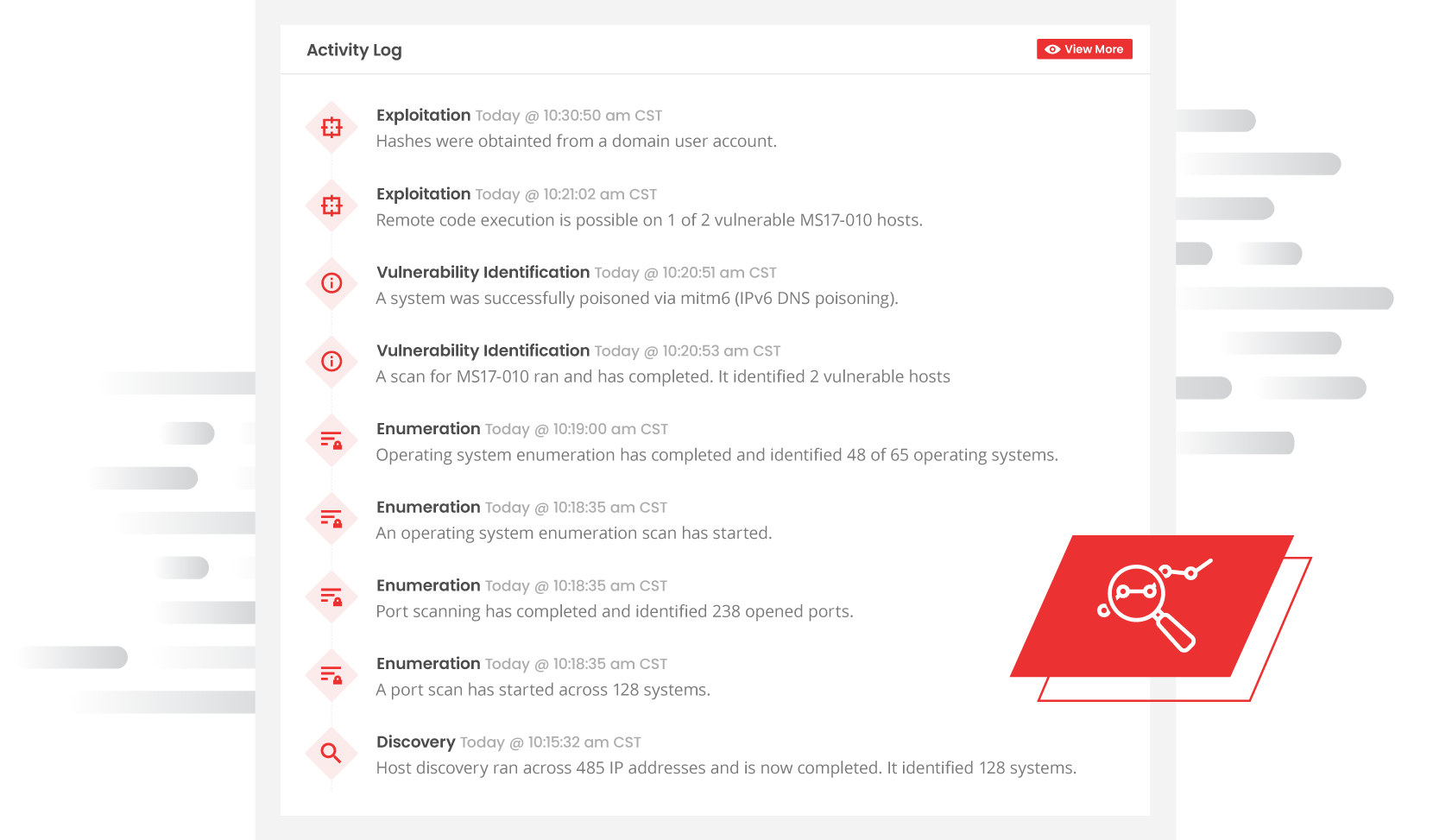
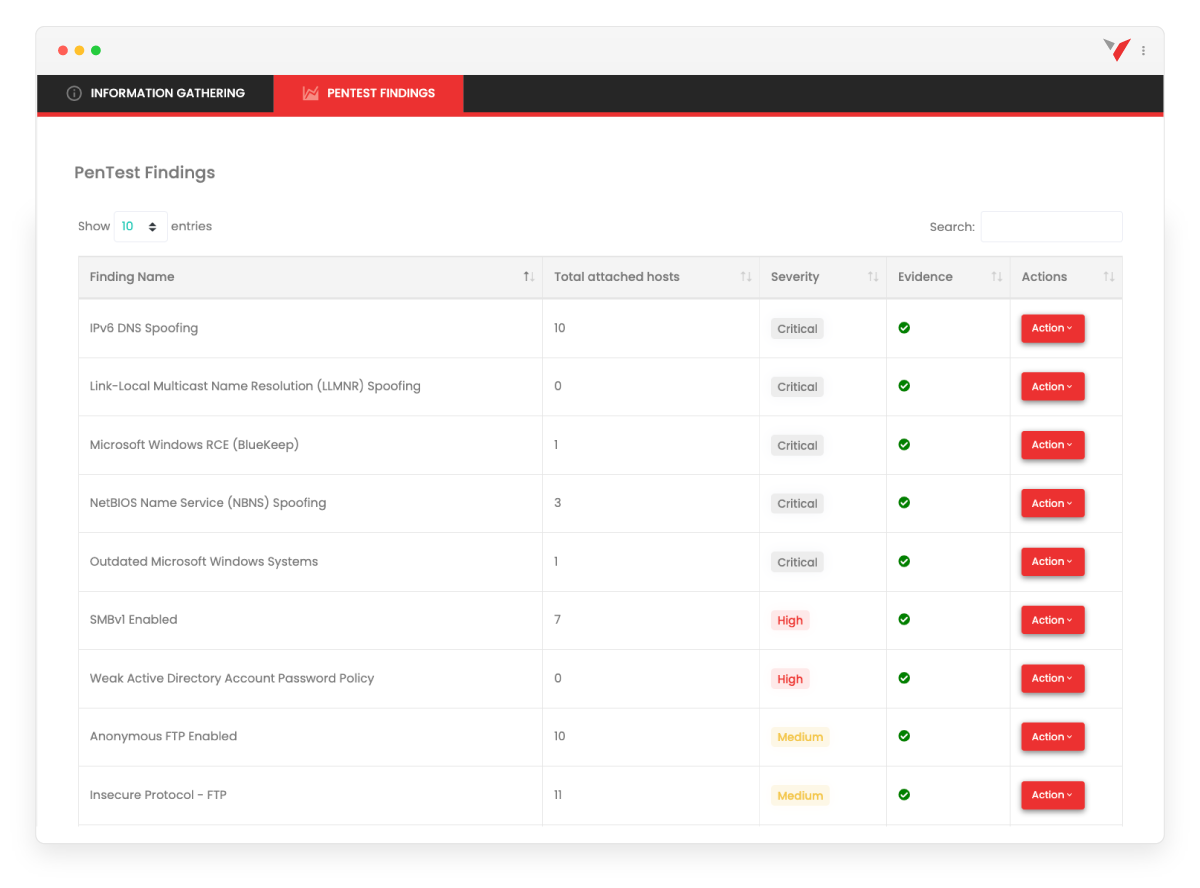
Real-time Visibility through your personal portal
Correlate our Activity Log with your SIEM and incident response procedures. Our real-time activity logs ensures your organization knows what’s happening and when. Find gaps in your security monitoring controls as the network penetration test occurs in real-time.
We make network penetration testing easy, efficient, scalable, and affordable for businesses that take cyber security seriously
Test your network monthly or as new threats emerge. Schedule a test within minutes and keep track of your organization’s risk profile in near real-time. Our reports will show you trending data, allowing your team to see improvements from one month to another.
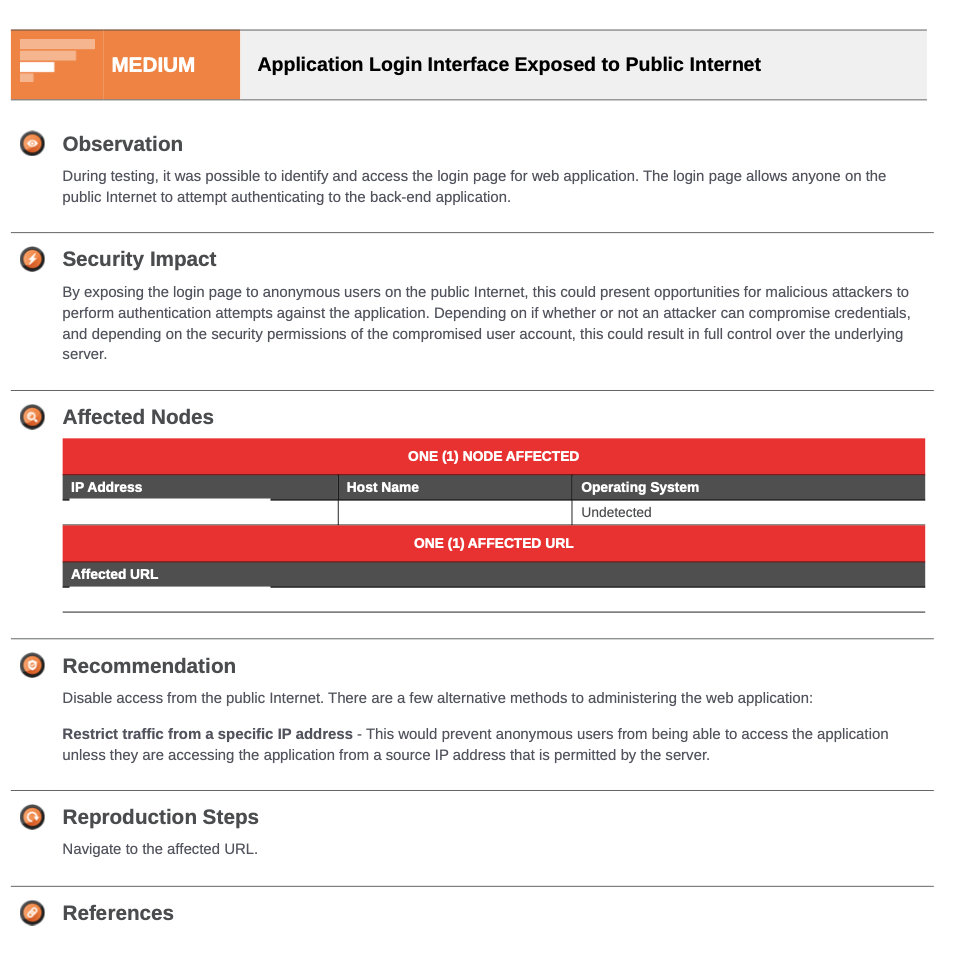
Full written report after every test
We provide a full written report on Host Discovery, Enumeration, Internal Network Environment Exposures, Security Impacts, Reputational Threat Findings, Discovered Threats, MITRE ATT&CK Mappings, and a complete Remediation Roadmap.
Complete Network Penetration Test Coverage
External Penetration Testing
The external network penetration test is performed from the standpoint of an external threat actor with limited knowledge of the target environment and without valid credentials to available services. Using a of automated testing methods, our tools will look to exploit identified vulnerabilities to bypass controls, and gain access to the system or gain access to your sensitive information.
Internal Penetration Testing
The internal network penetration test simulates an attack from within the organisation’s network, typically assuming the role of a trusted insider or a threat actor who has breached perimeter defences. This assessment is conducted with direct access to the internal environment, but without elevated privileges or valid credentials for sensitive resources. Through a combination of automated testing techniques, our tools will identify and attempt to exploit internal vulnerabilities to assess the strength of internal controls and the security of sensitive data.
Compliance Readiness
Meet compliance requirements with more scheduling flexibility and real-time alerts
With our solution, meet compliance requirements with more scheduling flexibility and real-time alerts. We provide more flexibility in schedule, alerting, real-time activity tracking, as well as segmentation testing to confirm isolation of sensitive networks. In addition to ensuring compliance readiness, we also test for security deficiencies that deviate from security best practices.
|
|
|
|